FreeBSD Gatewya/Router
Introduction
A D V E R T I S E M E N T
This guide takes takes you through the steps of setting up your FreeBSD box
to be your gateway/router. Some fundamentals of routing and networks is required
by the reader. I won't get into too much detail about the routing but you'd be
better off at least knowing the concpets.
FreeBSD Gateway Concepts
One of the most popular things to do is to use your PC and
FreeBSD to be the router for your home network. The concept is fairly straight
forward. You have 2 ethernet cards one for your 'inside' network and one for
your 'internet connection' or 'outside' network. You enable routing and wallah!
Conceptually, here is a map of how your network will look when you are done:
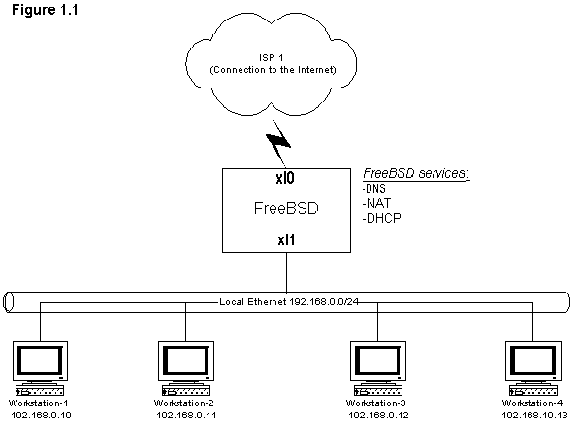
Adding a local network
First off, let's add a local network. This is sometimes
called an 'inside' or 'private' network. This do to the fact that the IP space (IPs
used on the network) are private and reserved (see RFC1918). Anyhow, In order to
add a 'private' network you need to add another ethernet card to your FreeBSD
machine. You need at least 2 ethernet cards to use this setup. Make sure you
install the both cards. Bring the machine up with both network cards installed.
In my example I use the xl0 interface as the 'outside' or 'public' ethernet
card. This xl0 card connects to my internet connection. In this example, I'm
using ethernet cards but they could be ANY interface (ppp, tun, gif, etc). I'm
using xl1 as my 'private' ethernet connection. The ordering is irrelevant. I
could have just as easily chosen xl0 to be my private and xl1 to be my public.
Make no difference.
Once you have both cards installed and they show up in
ifconfig output, you are set and ready to go. Configure the inside address as
some IP in your private IP space. In my example I chose to use 192.168.0.0/24 as
my RFC1918 private IP space. In reality it doesn't matter what IP range is used.
But for simplicity, I'm using 192.168.0.0 through 192.168.0.254. I assign an ip
to my xl1 card. I chose to use 192.168.0.1 as my BSD machines interface (once
again pick anyone out of your range of private IP space). If you don't know how
to set up the interfaces, please visit my
Interfaces page. Remember what IP you assign to the xl0 interface as you
will need it later. xl0 will have an IP from my ISP. Basically, leave xl0 alone.
We will be doing work on xl1 only.
Enabling gateway routing
Now time to tell BSD that it is OK to let packets get
forwarded or 'routed' between interfaces. This is accomplished by a sysctl
variable: net.inet.ip.forwarding. To set this:
# sysctl -w net.inet.ip.forwarding=1
This flag (when set to 1 meaning ON) tells the kernel it
is OK to forward packets between interfaces. Of course, this won't set it
permanently. You need to add an option to /etc/rc.conf:
gateway_enable="YES"
You just turned your machine into a ROUTER!!!
Client setups
Setting options in the clients TCP/IP settings is crucial
for this to work right. The idea is to have the client machines on the private
network (192.168.0.0/24) point the gateway to the IP you assigned to xl1 (In my
case it is 192.168.0.1). To do this, edit the client machine TCP/IP settings.
Add an IP from the range of 192.168.0.2 through 192.168.0.254, set the netmask
to 255.255.255.0 (/24), set the gateway address to the IP you assigned to your
xl1 interface (192.168.0.1). Add the DNS servers. If you setup DNS on your BSD
machine like shown in the
DNS section,
you can use your DNS server on your machine by putting the IP assigned to xl1 in
as the DNS server (In my case 192.168.0.1). If you didn't setup DNS on your BSD
machine, just use your ISP's DNS server. Although, I would recommend setting up
a caching-only nameserver for several reasons (all of which are out of scope for
this).
Before you go any further, make sure you can 'ping 192.168.0.1' from ALL YOUR
CLIENT MACHINES! Nothing irritating more than troubleshooting complex problems
when there is a simple problem.
NAT
At this point if you try to ping or goto an internet address
nothing will work. The reason for this is that when you send traffic to a
machine outside your private network, the packet gets sent to your default
gateway. The default gateway, in this case its your FreeBSD machine, sends the
packet unchanged out the xl0 interface to the internet (through your ISP). Well,
the problem with that is the IP space your are running on your inside network is
what they call 'nonrouteable'. In simple terms, it means that those IPs can't be
routed across the backbone of the internet. See RFC1918 for more detail.
So, we have a solution. It is called NAT. It changes your
private IP's to a public IP, sends it out, and when the packet comes back it
changes it back to the private IP that originally sent it. NAT is very complex
which is why I wrote a whole how-to on it. To set it up please read the
Nat Section
Testing your Solution
Testing is fairly straight forward. Try surfing with your
clients, checking mail, etc. If you run into problems, turn on logging on both
natd and with the firewall. Most of the time you missed something real straight
forward.
Another problem with NAT is that somethings just won't work
through NAT. Noteably, IPSEC VPNs, H323, and some chat/transfer programs. This
has to do with the stupidity of Microsoft and others but there are
workarounds...all of which are difficult to implement.
|
